
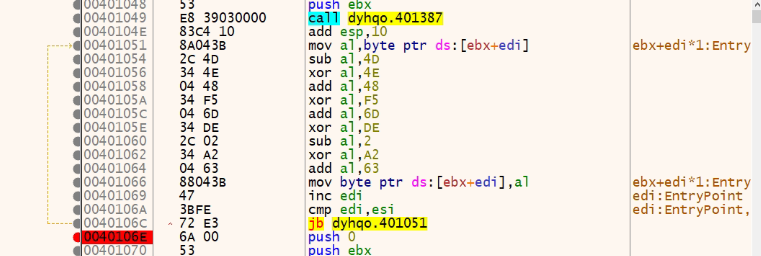
Threat actors have been using new techniques to hide their codes and avoid detection in every manner. They now use a new trend through NSIS (Nullsoft Scriptable Install System), which is an open-source installer that can bundle various files together. In the past, Malware attackers have used this NSIS-based crypter to hide themselves. This trend has been observed in malware families such as Lokibot, Ave Marie stealer, AgentTesla, Formbook, etc. This blog describes deeper insights into the new trend of cyber-attacks.
ANALYSIS- LOKIBOT
Let us look into the below hash (2D4739AB2D34EEC849D903E05E8E0EB4).
This is an NSIS file that can be identified through the DIE tool
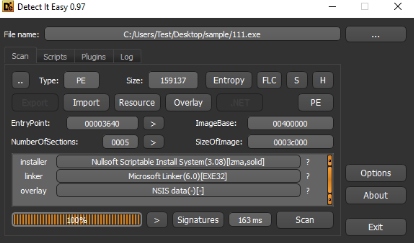
On extracting the file using 7zip, we can see the contents in the folder. It has two encrypted payloads and an executable inside it. On execution, all the files are dropped in the %temp% folder.
Let us now look into the executable jyacil.exe (MD5: 81EC4B73F581DD36CBDBB6C695CD038C). The file allocates memory using VirtualAlloc API and then copies the encrypted payload (botredmnra-6kb) into that allocated space.

This payload is decrypted into shellcode by the decryption loop followed.
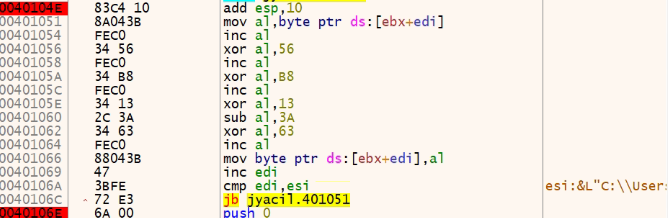
The code flow now moves into the decrypted shellcode, which is directly responsible for decrypting the bigger payload.
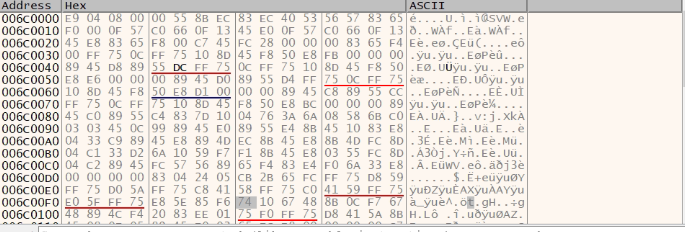
Now the bigger encrypted file is read from %temp% using ReadFile API and copied into virtually allocated memory. Then the file is decrypted by a big decryption loop whose chunks are present below. It is a massive loop, so only a few fragments are shown in the picture.
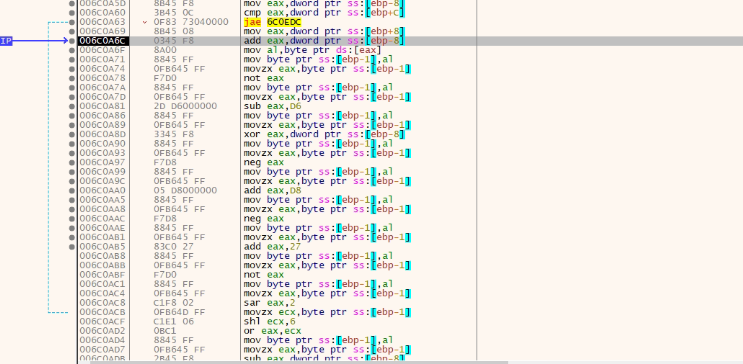
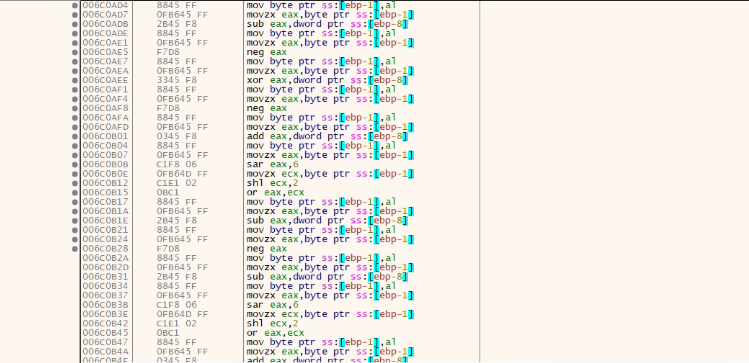
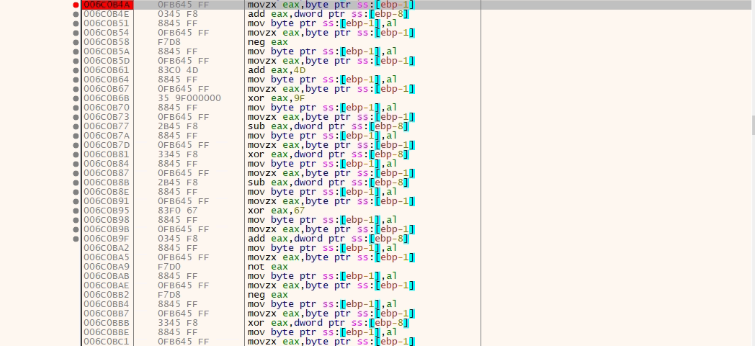
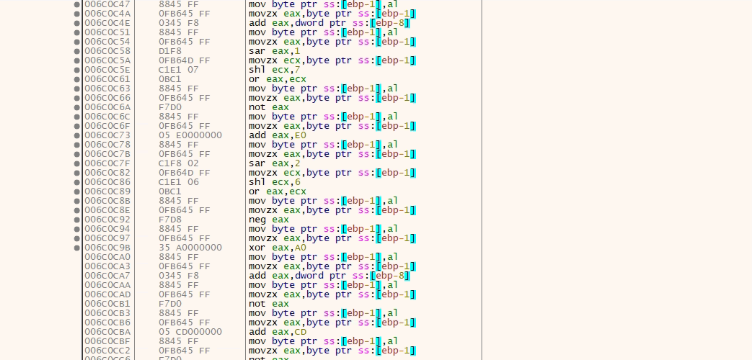
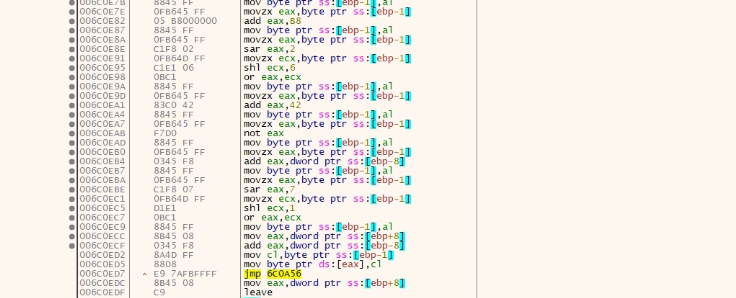
This decryption brings in another PE file which is the actual payload.
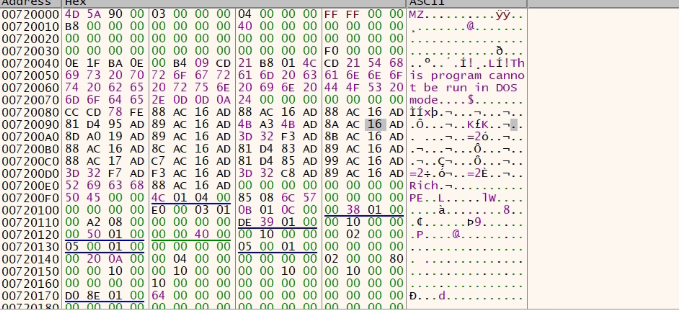
After this, process hollowing is done, and the actual malware payload performs its activity. Let us now focus on the actual malware (md5: C6085AED2E2C782F81CCCA6B5FACA13E[Visual C++ compiler]).
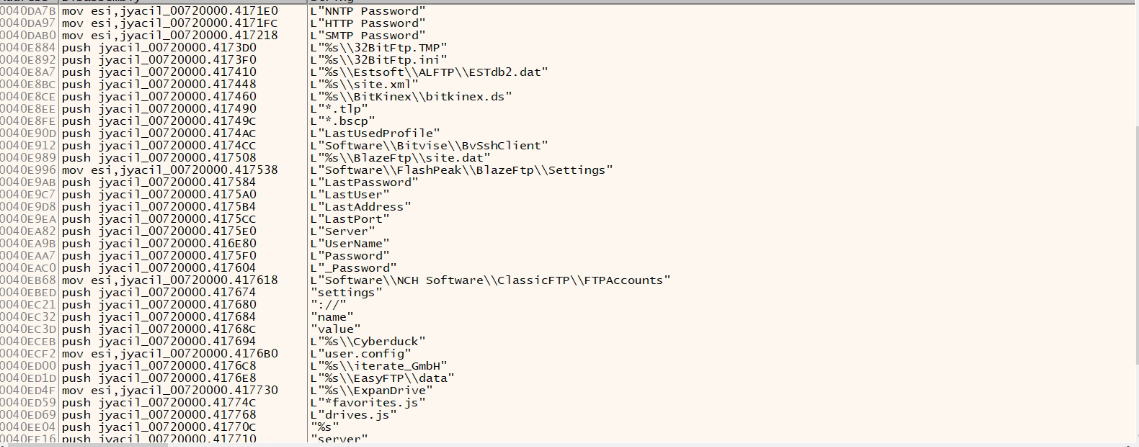
The malware creates a mutex to make sure only one instance is running. It then creates a file <randomname>.tmp to store all stolen information. This random name is formed by two unique strings present in the file.
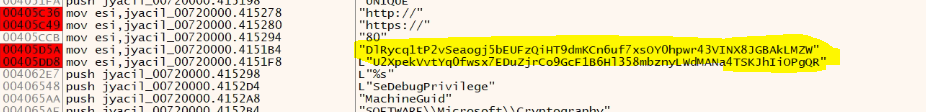
The C2 URL is hardcoded, which is later decrypted.
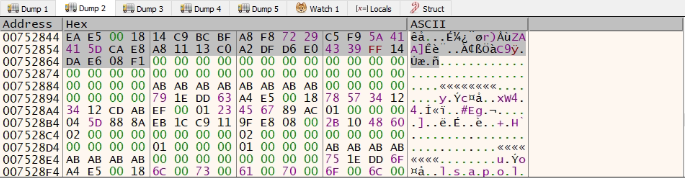
This payload is Lokibot stealer, which steals credentials from:
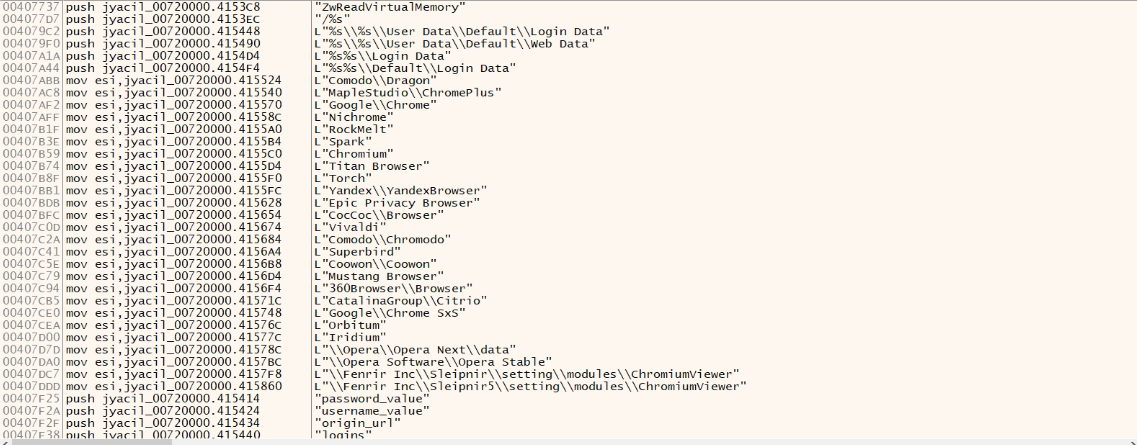
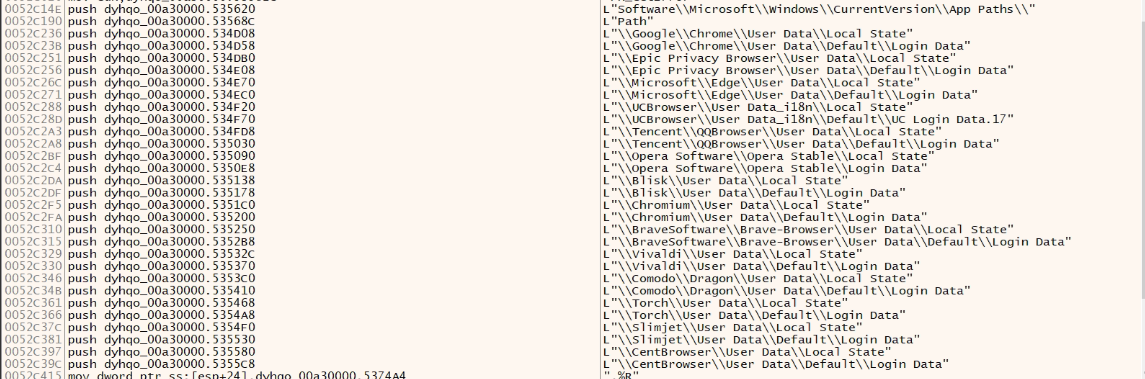
Comodo, Maplestudio, Google Chrome, Nichrome, RockMelt, Spark, Chromium, Titanium Browser, Yandex, Torch, Mustang Browser, NetSarang, FossaMail, Postbox, MoonChild, NetGate, Total Commander, EasyFTP, FileZilla, KiTTy, etc. and sends to C2 :
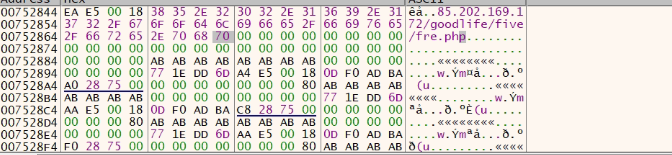
Hxxp[:]//85.202[.]169.172/goodlife/five/fre[.]php
ANALYSIS- Ave Marie Stealer
We now look into another file belonging to Ave Marie Stealer (MD5: CE488BABC73497C16CE8D2DE5ED218A7). This is also an NSIS-based file.
Using 7zip, we can see the contents present inside the file:
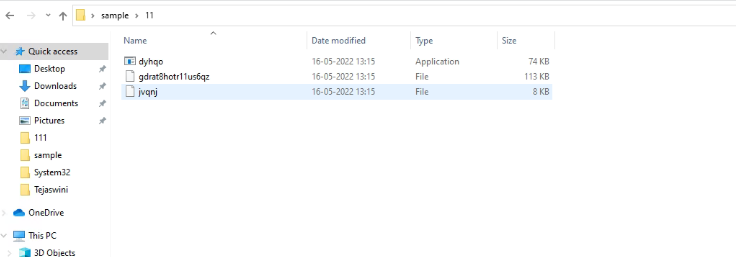
In this case, dyhqo.exe is responsible for decrypting the jvqnj (8kb file) and forms a shellcode which later decrypts the bigger payload gdrat8hotr11us6qz, which is the actual payload.
There is a slight change in the decryption loop in the first stage (The remaining file is almost the same):
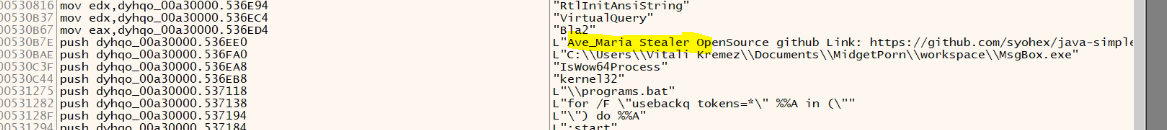
After the second stage decryption, we get the Ave Marie stealer (Delphi file) (MD5: E77D247BB34818C0C3352762C7DE0213). Related strings can be seen in the figure. This stealer captures keystrokes and steals data from various browsers such as UCBrowser, CentBrowser, Comodo, Chromium, Blisk, Microsoft Edge, etc.

ANALYSIS: AGENTTESLA
Let us now look into another file belonging to Formbook (MD5: 66BE80324D7937C5E17F5D4B08574145). This is also an NSIS based file.
Using 7zip, we can see the contents inside the file:
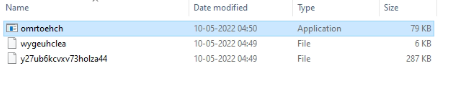
In this case, also omrtoehch.exe is responsible for decrypting the wygeuhclea (6kb file) and forms a shellcode which later decrypts the bigger payload y27ub6kcvxv73holza44, which forms the actual payload.
There is a change in the decryption loop in the first stage (The remaining file is almost the same). It is a big loop, so chunks of code are shown below:
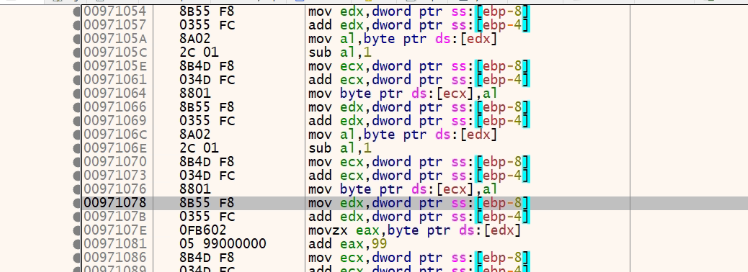
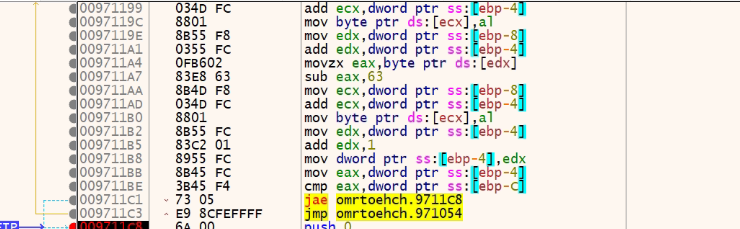
After the second stage decryption, we get another payload (Visual C MD5: D0FF8F95A6AA286D781528197255B805). In this file, it can be clearly observed that there is another PE file inside the resources (RCDATA). Let’s extract that and look into what exactly it is (F2E113BE23813F22EAA3B82CCBE535EA).
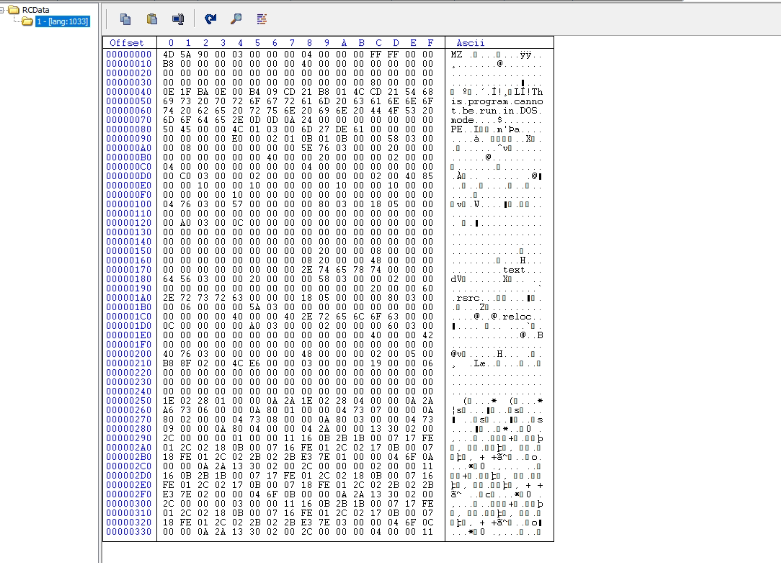
This file is a DOTNET file obfuscated by “Obfuscar, “which is an open-source .Net Obfuscator.
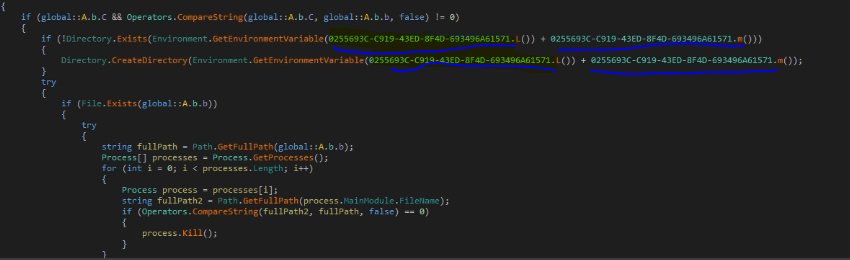
The code is highly obfuscated, and each string is decrypted at runtime. The encoded strings are highlighted. All the characters are stored in a single array of bytes, accessed by <<EMPTY_NAME>>
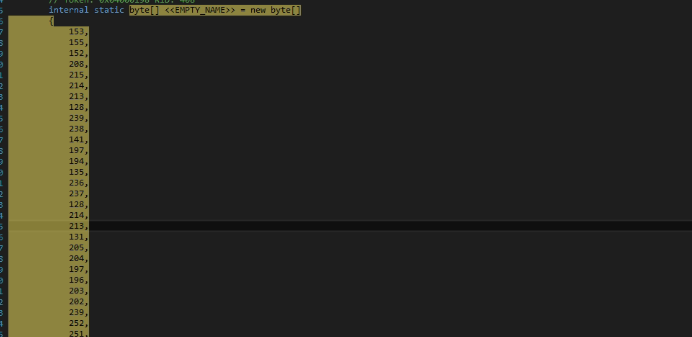
The decryption is done by the above list by XOR operation with the encrypted byte, its position on the list, and the decimal number 170.
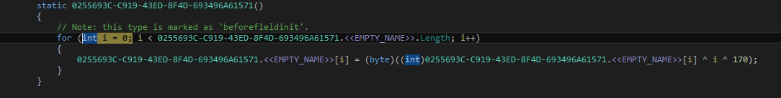
This payload, to access a string, will call the function that returns the string by accessing its position in the list and its length.
After decrypting the payload, the following strings were found, which are related to AgentTeslaV3:
\Account.CFN
\Account.stg
\accountrc
\accounts.xml
\Accounts\Account.rec0
\Accounts_New
\Apple Computer\Preferences\keychain.plist
\browsedata.db
\cftp\Ftplist.txt
\Claws-mail
\clawsrc
\Common Files\Apple\Apple Application Support\plutil.exe
\Comodo\IceDragon\
\CoreFTP\sites.idx
\Data\Tor\torrc
\Default\
\Default\EncryptedStorage
\Default\Login Data
\drivers\etc\hosts
\EncryptedStorage
\falkon\profiles\
\Mailbox.ini
\Microsoft\Credentials\
\Microsoft\Edge\User Data
\Microsoft\Protect\
\Moonchild Productions\Pale Moon\
\Mozilla\Firefox\
\Mozilla\icecat\
\Mozilla\SeaMonkey\
\NETGATE Technologies\BlackHawk\
\OpenVPN\config\
\Opera Mail\Opera Mail\wand.dat
\passwordstorerc
INFECTION VECTOR
All these files have the following infection chain
EMAIL >> DOCUMENT/XLS/CAB/RAR >> NSIS Installers
How does Quick heal protect its customers?
Quick heal protects its customers via following detections:
- IgenericPMF.S28122388
- NSISFrmbk.S26708217
- NSISLokibt.S26708218
- MsilFC.S17872954
- GenericRI.S28136194
Conclusion:
We observed a change in how malware actors deploy malicious code via NSIS installers. We can witness how the stealers discussed above are using NSIS based Loaders. All these loaders have a script in which code is embedded, where the exe file is executed with a random name encrypted payload (small size). The exe reads the smaller encrypted payload and decrypts it. Then the decrypted shellcode decrypts the larger file having a random name which forms the actual malware.
Thus, users should remain aware of these NSIS installers that might contain stealers these days.
Don’t hesitate to contact us:
Geetika Technosoft Pvt Ltd
E-mail: crm@gtechnosoft.in
T: 1800 212 6124
#GeetikaTechnosoft
#DasITCart
#DITC
#CustomerFirst
#ManagedITService
#FieldITService
#ITExpertsConsultation
#GloablITServiceProvider
#Quality
#Trustworthiness
#QuickHeal




More Stories
Telecom companies want OTT players to pay for 5G infrastructure, plan to go to DoT and TRAI
Google Maps to expand ‘Immersive View’ to routes: What it means, and the cities getting it
Google’s ChatGPT rival Bard gets new features, drops waitlist in 180 countries and more