
Microsoft has reported a zero-day vulnerability, designated CVE-2021-40444, whose exploitation enables remote execution of malicious code on victims’ computers. Worse, cybercriminals are already using the vulnerability to attack Microsoft Office users. Therefore, Microsoft is advising Windows network administrators to employ a temporary workaround until the company can deploy a patch.
CVE-2021-40444 details
The vulnerability is in MSHTML, Internet Explorer’s engine. Although few people use IE these days (even Microsoft strongly recommends switching to its newer browser, Edge), the old browser remains a component of modern operating systems, and some other programs use its engine to handle Web content. In particular, Microsoft Office applications such as Word and PowerPoint rely on it.
How attackers are exploiting CVE-2021-40444
The attacks appear as embedded malicious ActiveX controls in Microsoft Office documents. The controls enable the execution of arbitrary code; the documents most likely arrive as e-mail message attachments. As with any attached document, attackers have to persuade victims— to open the file.
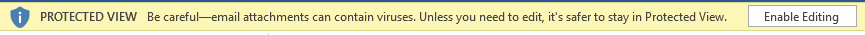
In theory, Microsoft Office handles documents received over the Internet in Protected View or through Application Guard for Office, either of which can prevent a CVE-2021-40444 attack. However, users may click the Enable Editing button without pausing to think, thus disarming Microsoft’s security mechanisms.
How to protect your company from CVE-2021-40444
Microsoft has promised to investigate and, if necessary, release an official patch. That said, we do not expect a patch before September 14, the next Patch Tuesday. Under normal circumstances, the company would not announce a vulnerability before the release of a fix, but because cybercriminals are already exploiting CVE-2021-40444, Microsoft recommends employing a temporary workaround immediately.
The workaround involves prohibiting the installation of new ActiveX controls, which you can do by adding a few keys to the system registry. Microsoft provides detailed information on the vulnerability, including a Workarounds section (in which you can also learn how to disable the workaround once you no longer need it). According to Microsoft, the workaround should not affect the performance of ActiveX controls already installed.
For our part, we recommend:
- Installing a security solution at the corporate mail gateway level or enhancing Microsoft Office 365’s standard security mechanisms to protect corporate mail from attacks;
- Equipping all employee computers with security solutions capable of detecting vulnerability exploitation;
- Raising employee awareness of modern cyberthreats on a regular basis, and in particular, reminding them never to open documents from untrusted sources, much less turn on editing mode unless absolutely necessary.
Source: CVE-2021-40444 zero-day vulnerability in Microsoft Office (kaspersky.com)
Don’t hesitate to contact us:
Geetika Technosoft Pvt Ltd
E-mail : crm@gtechnosoft.in
T: 1800 212 6124
#GeetikaTechnosoft
#ManagedITService
#ITExpertsConsultation
#GloablITServiceProvider
#Quality
#Trustworthiness
#Kaspersky
#ActiveX
#InternetExplorer
#Microsoft
#Office
#Vulnerabilities




More Stories
Telecom companies want OTT players to pay for 5G infrastructure, plan to go to DoT and TRAI
Google Maps to expand ‘Immersive View’ to routes: What it means, and the cities getting it
Google’s ChatGPT rival Bard gets new features, drops waitlist in 180 countries and more